Swagshop
-
Initial scans show swagshop is hosting a web server on port 80. Upon investigation, it's running Magento version 1.9x after digging deep into the xml files and cross referencing using Google.
Source file: http://10.10.10.140/skin/frontend/default/default/css/styles.css
Version confirmation: https://magento.stackexchange.com/questions/60476/determine-magento-version-without-access-to-code-base
-
I used
dirbusterto dig into what other possible folders are accessible.dirbustershowed a number of accessible folders and the two that stood out was:http://swagshop/downloader/ - Magento Downloader
http://swagshop/index.php/admin - Magento Admin Portal
I didn't have much experience with Magento so I found the Downloader first. Brute forcing the username and password didn't produce any results as I believe it banned my IP during my attempt.
-
One thing I learned from the
dirbusterresults was that index.php can be searched as well usingdirbuster. I received this hint through the HTB discord chat and I did not realize you can do this. I thought these two links are the same but it's not:You will see next how this information is important.
-
I started to search for possible Magento exploits on exploits-db. There are a lot of exploits to read through but most seem to be targeting version 2.0+. In addition, my mistake during my search on exploit-db was searching only verified exploits. I began to realize that unverified exploits also add to the missing pieces of this swagshop puzzle.
https://www.exploit-db.com/exploits/37977
Pay attention to the index.php in the target variable. Without this part, you cannot exploit Magento. I was struggling with this part as mentioned above. It was an oversight on my end.
-
Once the script has been executed, it will create Magento admin credentials of
forme:forme. -
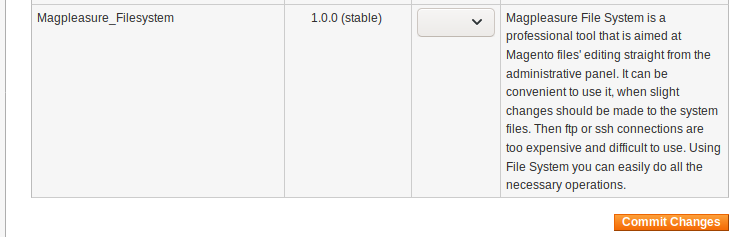
Now I needed to find a way to edit files just like how you would on a Wordpress site. A quick Google search shows you can install plugins. This is great because now you can install a File Manager type plugin and make our life easier.
https://pluginarchive.com/magento/magpleasure_filesystem
Download and install the plugin using the Magento Downloader control panel.
-
Once activated, use the Magento Admin control panel and navigate to:
System > Filesystem > IDEModify the
errors/503.phpwith your own PHP reverse shell code and save the file.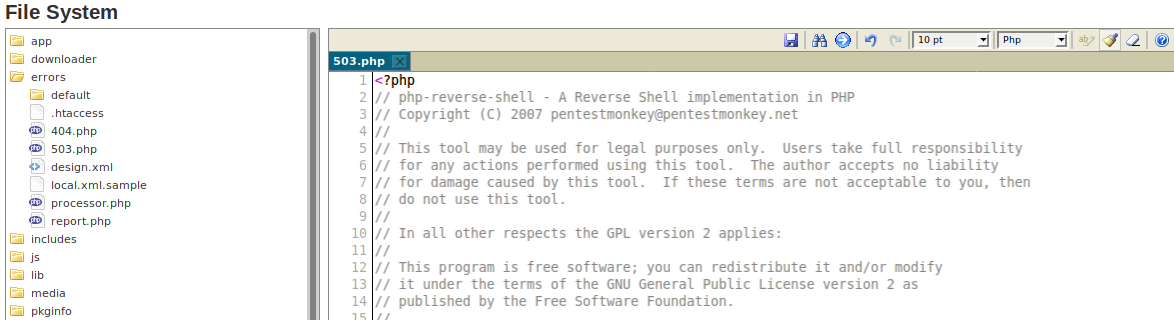
-
Start netcat to catch reverse shell:
nc -nvlp 4444 -
Use firefox and navigate to http://10.10.10.140/errors/503.php and a reverse shell has been established. Obtain user flag.
Privilege Escalation
-
After enumerating the machine using
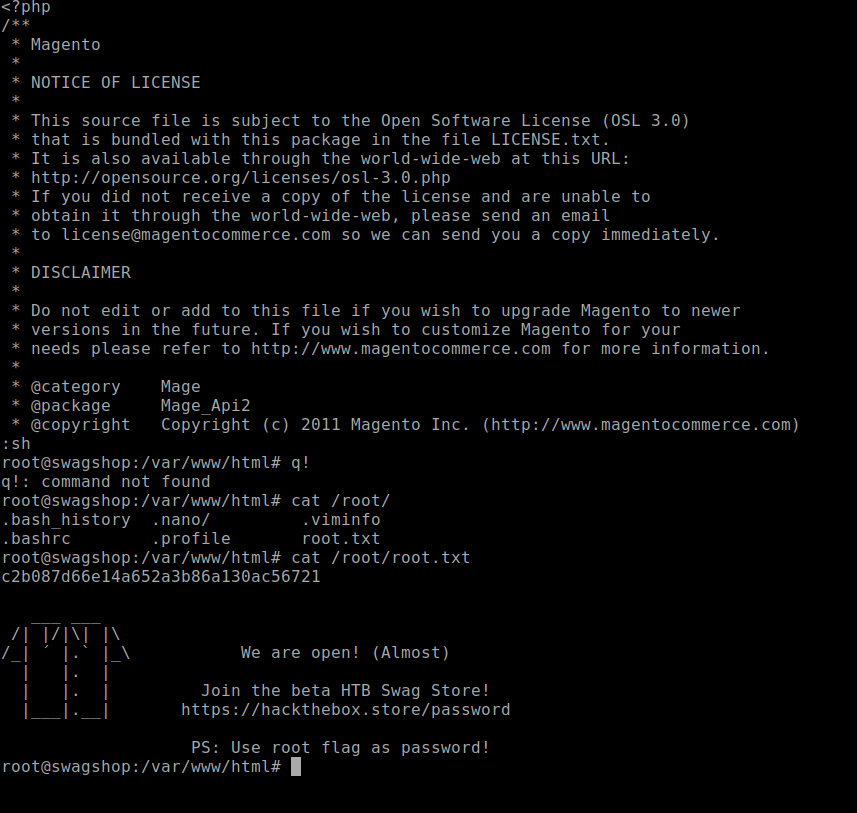
LinEnumscript, I noticed the sudoers file has been misconfigured:User www-data may run the following commands on swagshop: (root) NOPASSWD: /usr/bin/vi /var/www/html/* -
This means sudo vi will work in /var/www/html folder and you will obtain root flag.
sudo vi /var/www/html/api.php :sh